
The hidden costs of unchecked code
Financial risk exposure
Direct monetary losses from security breaches, regulatory fines, legal liability, and incident response costs.
Customer confidence
Erosion of client trust due to quality issues, compliance failures, and reliability problems that directly impact customer acquisition costs.
Competitiveness
Slower time-to-market allows competitors to capture market share and respond faster to customer demands.
Operational scalability
Inability to scale efficiently as technical debt accumulates, requiring exponentially more resources to maintain and extend systems.
Software Integrity
What is Security Code Review
Expert security engineers analyze your source code to find vulnerabilities and design flaws before production. With deep software knowledge, they identify how attackers could compromise your systems and help fix issues early, when remediation is fastest and cheapest.
Full stack security





...
Frontend
We review client-side code to identify insecure input handling, weak session management, and exposure of sensitive data, ensuring robust validation and secure frameworks prevent common attacks like XSS and CSRF.





...
Backend
Our analysis focuses on business logic flaws, unsafe data processing, and misconfigurations in APIs and services. A secure backend protects critical assets and ensures data integrity.





...
Infrastructure
We audit manifests, charts, and scripts for misconfigurations, privilege escalation risks, and supply chain vulnerabilities. A secure infrastructure foundation prevents deployment-time breaches and resists attacks at runtime.
Inside our review process
Our experts use internationally recognized testing frameworks and methodologies to audit your code and uncover critical vulnerabilities throughout your technology landscape.
Automated security scans
Quickly detect code and dependency risks using SCA and SAST for rapid, reliable insights.
+
Expert manual review
In-depth analysis using OWASP standards and best practices to validate findings and uncover hidden flaws.
=
Complete security approach
Combines automation and expert review for accurate, actionable results and long-term security.
Let us secure your tech stack together.
Every line of code matters. Schedule a consultation with our security specialists to discuss your code review needs.

Common assessment areas
Each assessment area represents a critical security domain we thoroughly audit and strengthen to eliminate attack vectors before they can be exploited.
Authentication & Session Management
Logging & Error Handling
Authorization & Access Control
Encryption & Secret Management
Infrastructure Definitions & Configuration Scripts
File Handling & Transfer
Payments & Transaction Processing
Data Validation & Input Sanitization
Dependencies & Third-party Libraries
API Endpoints & Integration Interfaces
Why companies choose Security Code Review
Competitive Edge
Deliver confident product launches while competitors deal with post-release security incidents.
Trust & Reputation
Build customer confidence and protect brand reputation by demonstrating proactive security leadership to clients and partners.
Compliance
Ensure compliance through auditable evidence for relevant regulatory requirements, such as SOC 2, PCI DSS, and GDPR.
Business Continuity
Identify operational threats before deployment, prevent costly downtime and maintain the stability essential for predictable revenue.
What you receive

Executive Report
A business-oriented summary, empowering informed decisions at the executive level.

Executive Presentation
A visual presentation facilitating effective communication and alignment for senior stakeholders.
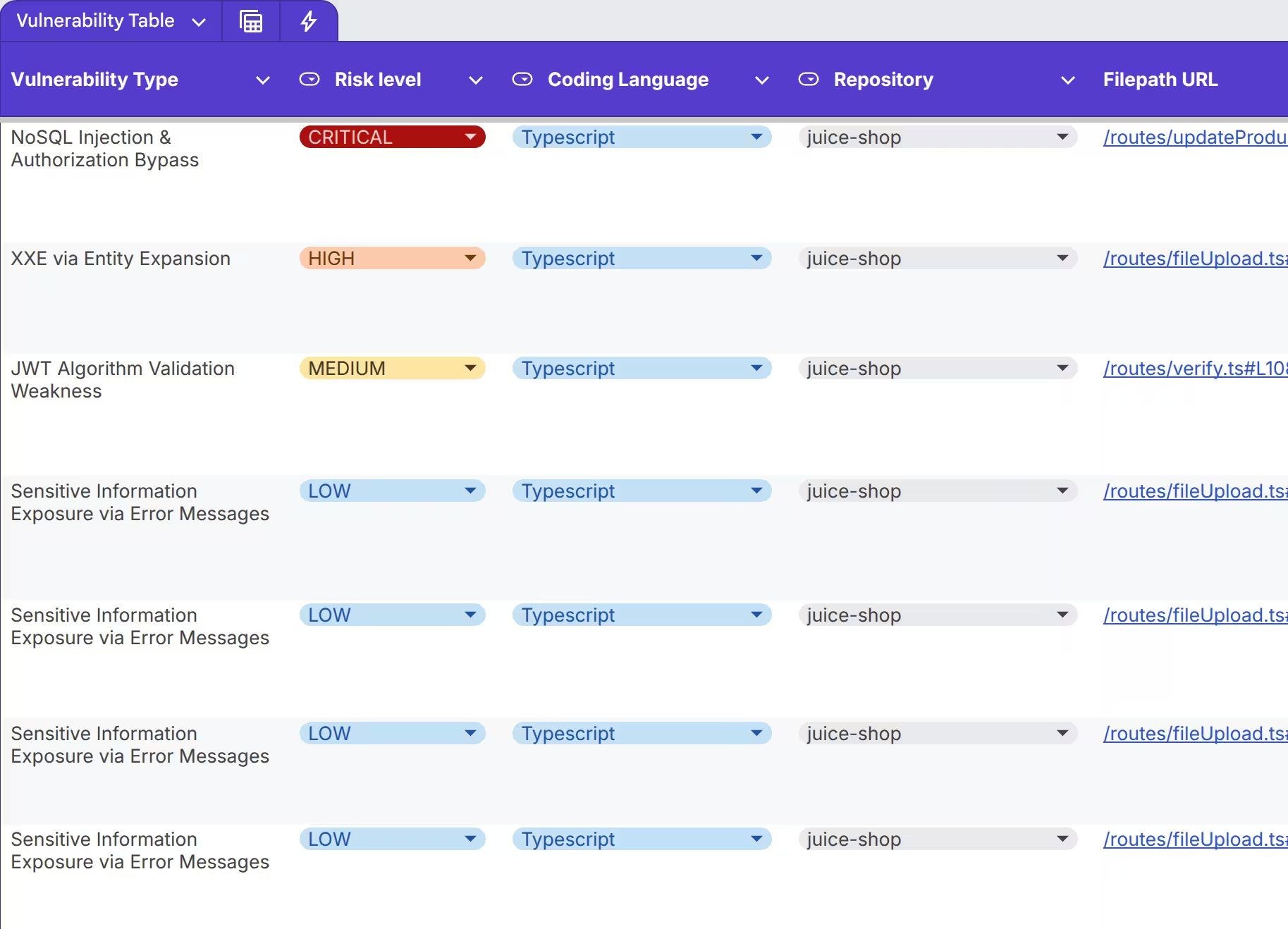
Vulnerability Matrix
A detailed record of every vulnerability found, mapped to compliance, risk and remediation contexts.
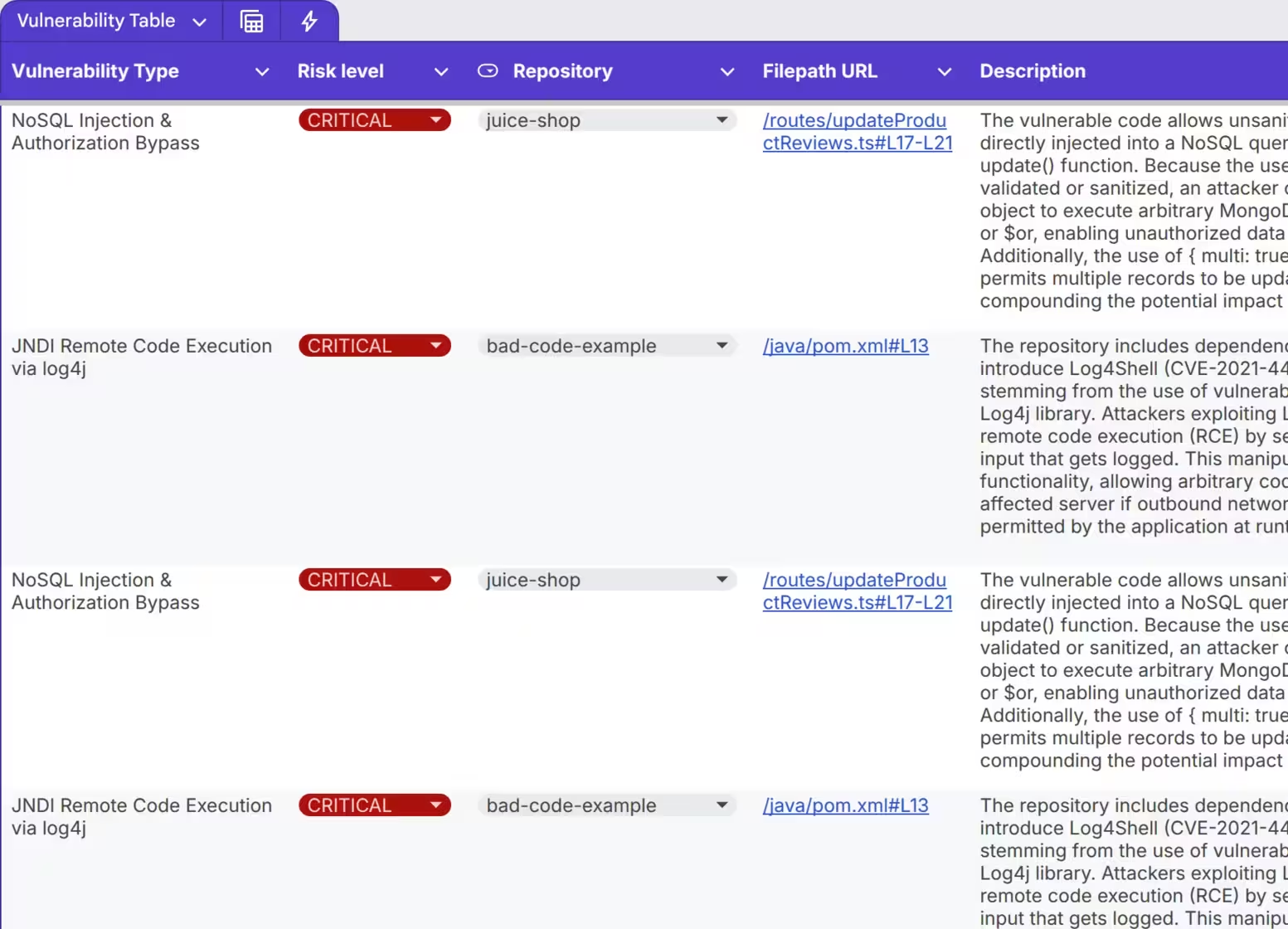
Critical Vulnerability Matrix
Real-time visibility of the most critical security issues to enable rapid remediation.
Transform vulnerabilities into strengths.
Get actionable remediation guidance backed by offensive security expertise and prioritized by real-world attack impact.

Roles and responsibilities
Team Lead
Leads the security code review lifecycle, from planning to final report. Validates findings, ensures actionable remediation, and oversees adherence to secure coding standards. Acts as the main technical contact for updates, clarifications, and strategic recommendations.
Security-First Engineer
Executes core security code review activities, including identification of insecure coding patterns, logic flaws, and potential vulnerabilities. Documents findings in detail and compiles the technical report, ensuring accuracy, clarity, and alignment with secure development best practices.
Project Manager
Oversees project initiation, scheduling, and day‑to‑day coordination. Manages communication between your stakeholders and the reviewing team, tracks deadlines and milestones, and ensures the engagement is delivered smoothly, on time, and within scope.
Compliance Auditor
Monitors alignment with key regulatory frameworks (such as SOC 2, ISO 27001, PCI DSS, HIPAA, and GDPR) and your internal policies. Reviews methods and evidence to confirm that the engagement meets legal, contractual, and audit requirements.
Our recent success story
Challenge
Despite having advanced perimeter security, the organization's proprietary source code, consisting of 63,000 lines of code across 22 repositories, remained exposed to hidden critical vulnerabilities and risks due to introduction of AI-generated "vibe" code.
Approach
Enterprise-grade static analysis uncovered code flaws, outdated dependencies, and misconfigurations, while senior engineers manually reviewed all modules to discover business-logic vulnerabilities that automation cannot find.
Results
Discovered 1,274 vulnerabilities of which 367 were of critical risk level. Each flaw was ranked by remediation priority, providing the company's first complete application-layer exposure view and giving development teams an actionable security roadmap for compliance.
Impact
The tailored remediation roadmap increased visibility by 85%, cut the organization's projected breach exposure by 95% and strengthened stakeholder confidence to secure budget, streamline internal operations and align the company with regulatory expectations.
Frequently asked questions.
Find answers to common questions about our security code review service.
How does the code review process work?
Our specialized security engineers analyze your source code using a combination of automated Static Application Security Testing (SAST) tools, Software Composition Analysis (SCA) tools, and expert manual review. We identify vulnerabilities, insecure coding patterns, and design flaws, then deliver comprehensive reports with prioritized remediation guidance.
Do you require access to our source code?
Yes. Security code review requires read-only access to your application's source code repositories. We work under strict confidentiality agreements and follow secure handling protocols to protect your intellectual property throughout the engagement.
Will this disrupt our development workflow?
No. Code review is performed on a snapshot of your codebase and does not interfere with active development. We can coordinate reviews during sprint planning cycles to minimize impact on release schedules.
How do you prioritize and rate the findings?
We move beyond simple severity scores. Findings are prioritized by real-world attack impact and remediation urgency. Our analysis separates critical risks from noise, providing a vulnerability matrix that allows your team to focus immediately on the flaws that expose you to financial risk or data breaches.
Do you collaborate with our developers on remediation?
Yes. We provide fix patterns, code snippets, and engineering Q&A sessions. Follow‑up validation or re‑testing can be scoped as a separate engagement.
Is it a one‑time exercise or an ongoing practice?
It is most effective as an ongoing practice: at major releases, after significant architectural changes, and for high‑risk components on a recurring cadence.
Is it suitable for compliance and audits?
Yes. Our code review deliverables provide auditable evidence for compliance frameworks such as SOC 2, PCI-DSS, ISO 27001, GDPR, and HIPAA. Reports map findings to relevant security controls and regulatory requirements.
Ready to harden your codebase?
Our expert team is prepared to conduct a comprehensive security assessment tailored to your application architecture.
