
What you are missing without a real attack plan
No regular pentests means no evidence‑driven roadmap for what to fix first, where to invest, and which risks actually matter.
54%
4.88M
Attacks on known vulnerabilities
Average cost of a data breach
Blind Spots
Critical weaknesses stay hidden until real attackers exploit them.
Unproven Security
Controls look strong on paper but fail under attack.
Compliance Risk
Missing independent tests blocks certifications, renewals, and key deals.
Recurring Flaws
Same vulnerabilities reappear because fixes are never verified.
Beyond Automation
Penetration Testing Explained

Penetration testing, or ethical hacking, is a proactive security exercise where our certified experts simulate real-world cyberattacks on your systems. Unlike automated scans, we think like hackers to uncover complex vulnerabilities that tools miss.
Audit exposed surfaces, validate active defenses
Comprehensive penetration testing across apps, cloud, networks, and people to expose real attack paths.
Mobile application
Secure mobile apps against real-world attacks, data leaks, and compliance risks.
Web application
Uncover and fix web vulnerabilities before attackers exploit your sites and users.
Desktop application
Validate desktop apps against data abuse, access misuse, and regulatory exposure.
Cloud infrastructure
Expose misconfigurations and risky paths in cloud environments before they impact you.
API
Harden APIs against abuse, data exposure, and lateral movement across your ecosystem.
Internal & external network
Reveal weaknesses in internal and external networks before attackers can pivot.
Web3
Stress-test smart contracts and Web3 logic against exploits, fraud, and market abuse.
Social engineering
Simulate phishing, pretexting, and baiting to measure and improve human defenses.
Anti-drone system
Assess and optimize anti-drone detection, response, and countermeasures for threats.
SCADA / OT
Protect SCADA and OT systems from network, protocol, and operational disruptions.
IoT
Test IoT devices, networks, and cloud backends against real-world compromise.
Do not wait for a breach to test your defenses.
Secure your assets with Cyberware's expert penetration testing.

Uncovering OWASP Top 10 threats
Identify the vulnerabilities that matter most, prioritized for immediate action.
Broken Access Control
Security Misconfiguration
Software Supply Chain Failures
Cryptographic Failures
Injection
Insecure Design
Authentication Failures
Software or Data Integrity Failures
Logging & Alerting Failures
Mishandling of Exceptional Condition
Why organisations rely on us
Enterprise proven
Trusted by banks, critical infrastructure, and global brands to test their most sensitive systems under real attack conditions.
Adversary insight
Specialists who think like real attackers to reveal the weaknesses most likely to be exploited in the wild.
Actionable findings
Clear, prioritized reports that translate technical issues into business risk, so your team knows exactly what to fix first.
Compliance ready
Assessment outputs mapped to frameworks like SOC2, ISO 27001, PCI‑DSS, HIPAA, and GDPR to support audits and security reviews.
What you receive

Executive Report
A business-oriented summary, empowering informed decisions at the executive level.

Executive Presentation
A visual presentation facilitating effective communication and alignment for senior stakeholders.
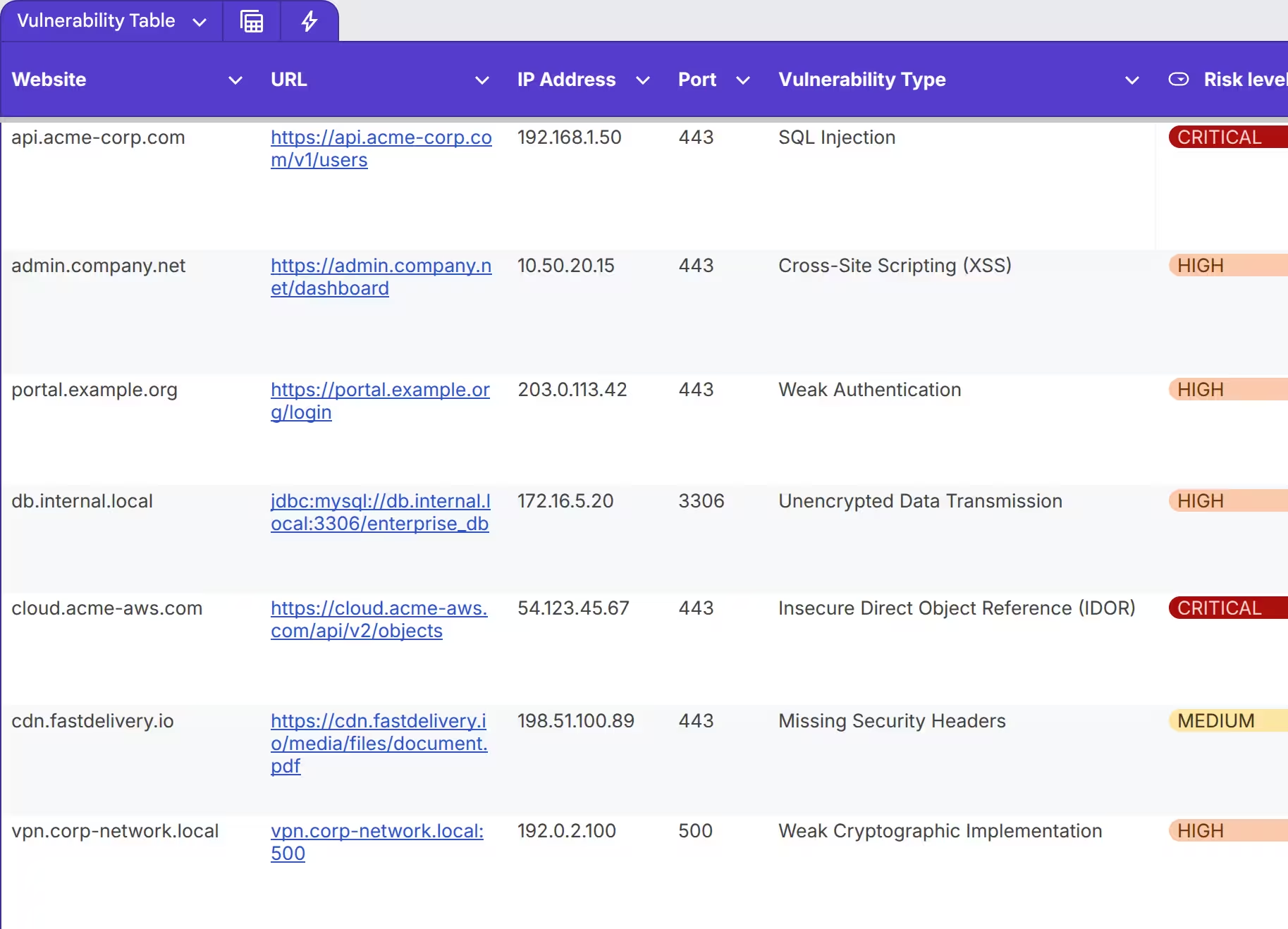
Vulnerability Matrix
A detailed record of every vulnerability found, mapped to compliance, risk and remediation contexts.
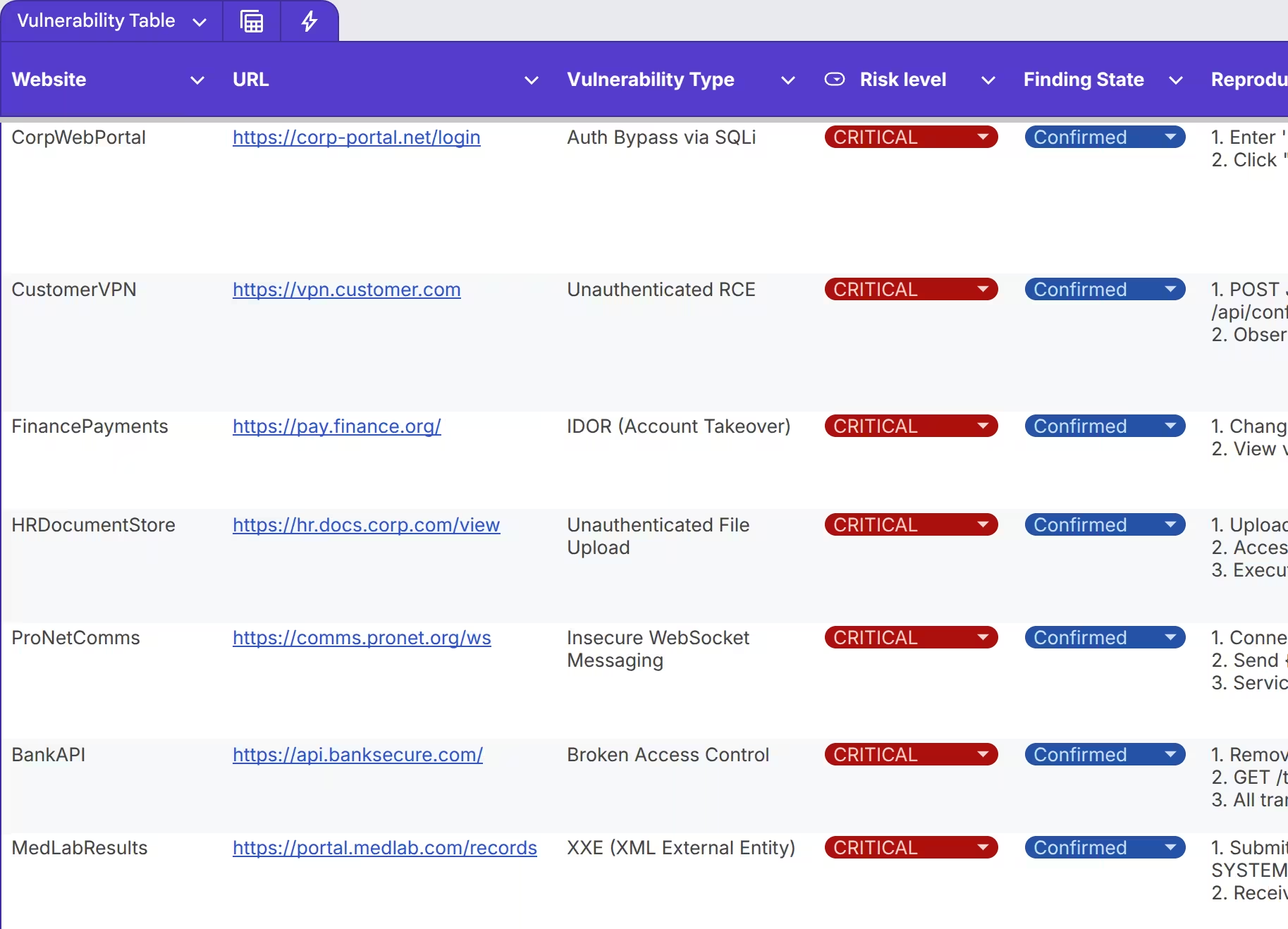
Critical Vulnerability Matrix
Real-time visibility of the most critical security issues to enable rapid remediation.
Get a comprehensive view of your security posture.
Identify blind spots and secure your infrastructure today.

Roles and responsibilities
Lead Penetration Tester
Leads the security testing lifecycle from planning to final report. Designs realistic attack scenarios, directs the testing team, and validates all findings. Acts as the main technical contact, explaining what was found, how it was discovered, and what it means for your business.
Security Consultant
Executes the core penetration testing activities, safely attempting to breach applications, cloud services, and internal systems. Identifies vulnerabilities, validates their real‑world impact, and documents everything in a clear technical report your defenders can act on.
Project Manager
Oversees project initiation, scheduling, and day‑to‑day coordination. Manages communication between your stakeholders and the testing team, tracks deadlines and milestones, and ensures the engagement is delivered smoothly, on time, and within scope.
Compliance Auditor
Monitors alignment with key regulatory frameworks (such as SOC 2, ISO 27001, PCI DSS, HIPAA, and GDPR) and your internal policies. Reviews testing methods and evidence to confirm that the engagement meets legal, contractual, and audit requirements.
Our recent success story
Challenge
The client needed to find all vulnerabilities and risks in their publicly available IT infrastructure including 36 domains, 56 subdomains, 20 IPs, 230 services, 110 components, and 5 public security layers. The results should be usable as evidence for compliance and adherence to laws.
Approach
Enterprise-grade automated analysis uncovered misconfigurations, outdated dependencies, and potential vulnerabilities, while senior pentesters manually assessed services to expose business-logic vulnerabilities and confirm potential ones, eliminating false-positives.
Results
Delivered thorough asset exposure visibility, discovering shadow IT in the process. Denial of Service, SQL Injections, Command Injections, and vulnerable third-party components were discovered and mapped to their respective risk levels. Thorough remediation plan was presented.
Impact
Successfully mitigated potential losses totaling $20 million by discovering and fixing key threats, including data breach, ransomware, intellectual property theft, social engineering, and denial of service all affecting critical or important systems.
Frequently asked questions.
Find answers to common questions about our penetration testing service.
How is penetration testing different from a vulnerability scan?
Vulnerability scans are automated tools that identify known weaknesses. Penetration testing involves skilled testers who actively exploit vulnerabilities, chain multiple issues into attack paths, and validate real-world risk, going far beyond what automated scanners can detect.
Will penetration testing disrupt my business operations?
We design our tests to minimize disruption. We can schedule aggressive testing during off-hours and coordinate closely with your team to avoid downtime.
What happens if you find a critical vulnerability during testing?
We immediately notify your designated contact and pause testing if needed. Critical findings are escalated in real-time so your team can assess and contain the risk while we continue testing other areas.
Do you provide re-testing after we fix the issues?
Yes, we offer a re-test verification to ensure that the identified vulnerabilities have been effectively remediated.
How often should we conduct penetration tests?
Most organizations conduct penetration tests annually or after significant changes such as major deployments, infrastructure updates, or new application releases. Regulatory frameworks like PCI DSS require annual testing.
Do your assessments support compliance and regulatory requirements?
Yes, our testing is aligned with major frameworks including SOC 2, ISO 27001, PCI DSS, HIPAA, and GDPR. The final report is structured to satisfy audit requirements, support certification efforts, and demonstrate due diligence to regulators.
Ready to test your defenses?
Contact us today for a free scoping call.
